As a member of the Linux Foundation Core Infrastructure Initiative, Cisco is contributing to the CII effort by evaluating the Network Time Protocol daemon (ntpd) for security defects. We previously identified a series of vulnerabilities in the Network Time Protocol daemon; through our continued research we have identified further vulnerabilities in the software.
Since 2013, criminals have been abusing NTP packets in order to cause amplified denial of service attacks. The ubiquity of the Network Time Protocol daemon and the importance of co-ordinated time for the correct functioning of many services means that it is a tempting target for attack. Vulnerabilities that allow the time as understood by ntpd to be altered can be used by attackers to set the time to an arbitrary value. This allows attackers to prevent time dependent services from starting because the time of activation is never reached, to provoke the depletion of system resources by repeatedly reaching the time of activation of services, to gain system access by using expired certificates, to deny service by expiring legitimate services and caches. Hence, the importance of identifying and remediating vulnerabilities within the time service.
Cisco has discovered six vulnerabilities within ntpd that allow attackers to craft UDP packets to either cause a denial of service condition or to prevent the correct time being set. We recommend that all users upgrade to the latest version of ntpd.
CVE-2016-1550 NTP Authentication Potential Timing Vulnerability
Discovered by Matthew Van Gundy and Stephen Gray of Cisco ASIG.
NTP packets, as described by RFC5905 can contain a Key ID, a 32-bit unsigned integer used to designate a secret 128-bit key which is shared between co-ordinating systems. This key is used to calculate a MD5 message digest value for the packet to authenticate the sender to the recipient.
If a mismatch is found between the digest within the packet and the value as calculated by the client using the secret key, the packet is rejected. The recipient sends a crypto-NAK packet to the sender to inform of the incorrect digest. However, the timing of the sending of this packet can be used to inform an observer where in the digest the mismatched occurred. Mismatches in the first bytes compared generate crypto-NAK packets sooner than mismatches in later bytes. Attackers can learn the value of the shared key by brute force attacking the MD5 digest and examining the timing of the returned crypto-NAK packets. Once the value of the key is discovered the attacker can send spoofed NTP packets that are authenticated as valid by the recipient.
Versions confirmed vulnerable:
ntp 4.2.8p4, NTPSec a5fb34b9cc89b92a8fef2f459004865c93bb7f92
Others may be affected as well.
CVE-2016-1551 NTP Refclock Impersonation Vulnerability
Discovered by Matt Street of Cisco ASIG in collaboration with others.
Ntpd implicitly trusts reference clock NTP traffic originating from the 127.127.0.0/16 network. This means that an attacker that successfully sends spoofed NTP packets from an IP address in the 127.127.0.0/16 range will be treated as trusted by systems that have been configured with a reference clock.
The network range 127.0.0.0/8 is private according to RFC1918, such traffic should not be encountered by ntpd but filtered out by the operating system or routers. If the attacker successfully delivers the spoofed packets and establishes themselves as a trusted peer of the target system, they can then use this relationship to alter the time of the target system.
In practice, such packets will rejected by most modern operating system before they are encountered by ntpd. In the case where an operating system does not reject such packets automatically, a firewall can be deployed to drop any packets the purport to originate from this range. Unless required, configuring daemons to listen on 127.0.0.0/8 should be discouraged to avoid vulnerabilities similar to this.
Versions confirmed vulnerable:
ntpd 4.2.8p3, NTPsec a5fb34b9cc89b92a8fef2f459004865c93bb7f92
Others may be affected as well.
CVE-2016-1549 NTP Ephemeral Association Sybil Vulnerability
Discovered by Matthew Van Gundy of Cisco ASIG.
The NTP protocol allows systems to create peer-to-peer associations with other systems to calculate a common system time rather than having an authoritative time value dictated by a reference clock via client-server relationship. These peer associations may be ephemeral in nature and created on the fly. The client will insist that before establishing a peer relationship that the connecting peer is authenticated using the key mechanism described earlier.
However, there is no limit on the number of peers that may share the same key. If an attacker discovers the identity of a key, possibly using the mechanism described in CVE-2016-1550, this key may be used to set up a large number of malicious peers. By advertising a consistent false time to the client, these malicious peers can cause the client to accept the false time as the correct value. In effect the large crowd of malicious peers can drown out the any correct time values shared by non-malicious peers.
Versions confirmed vulnerable:
ntpd 4.2.8p3, ntpd 4.2.8p4, NTPsec 3e160db8dc248a0bcb053b56a80167dc742d2b74, NTPsec a5fb34b9cc89b92a8fef2f459004865c93bb7f92
Others may be affected as well.
CVE-2016-1547 Demobilization of Preemptible Associations
Discovered by Stephen Gray and Matthew Van Gundy of Cisco ASIG.
In certain circumstances, the association of peer ntpd systems can be interrupted by sending spoofed packets which inform the recipient that an attempt to authenticate their request has failed. Crypto-NAK packets are sent when authentication fails, but are not themselves authenticated. Hence, an attacker can send crypto-NAK packets spoofed to originate from a legitimate peer forcing the recipient to break the association. By repeatedly sending spoofed crypto-NAK packets the attacker can prevent the peers from re-establishing their peer relationship causing a denial of service.
Versions confirmed vulnerable:
ntpd versions 4.2.8p3, 4.2.8p4, NTPSec a5fb34b9cc89b92a8fef2f459004865c93bb7f92
Others may be affected as well.
CVE-2016-1548 Xleave Pivot: NTP Basic Mode to Interleaved
Discovered by Jonathan Gardner of Cisco ASIG and, independently, by Miroslav Lichvar of RedHat
The NTP specification allows for an interleaved mode where one packet contains the timestamp of when the preceding packet was sent. This allows for greater accuracy in calculating the time required to process packets for sending.
An attacker can send a specially crafted packet in order to force a ntpd client to switch from basic client-server mode into interleaved mode even if the client is not configured to adopt interleaved mode. Once switched, the client will reject any further packets from a previously associated server, and an attacker can send further packets to set the time on the client to a value chosen by the attacker.
The vulnerability occurs due to mechanism by which ntpd checks incoming packets. In basic modes, the response packet sent on receipt of a request packet will contain the origin timestamp set to be the same as that of the transmit timestamp of the request. If this is not the case, ntpd checks if the packet is an interleaved packet before discarding it. If the origin timestamp is the same as the destination timestamp, the last time the client received a packet from the peer, then the client is placed in interleaved mode. To exploit the vulnerability, the attacker needs to know the destination timestamp. This value can be accessed via the ntpq query tool, inferred from data within response packets, or by obtaining the value through a brute force attack.
Versions confirmed vulnerable:
ntpd versions 4.2.8p4, NTPSec aa48d001683e5b791a743ec9c575aaf7d867a2b0c
Others may be affected as well.
Conclusion
The ntpd daemon is a vital part of many systems ensuring that system clocks are synchronised to a common standard. Cisco is committed to ensuring that these fundamental system components are free, as much as possible, of vulnerabilities. To this end, Cisco’s vulnerability research teams are responsibly disclosing these vulnerabilities after co-ordinating fixes with the relevant bodies. Administrators should apply patches or upgrade ntpd installations as soon as possible.
Mitigations
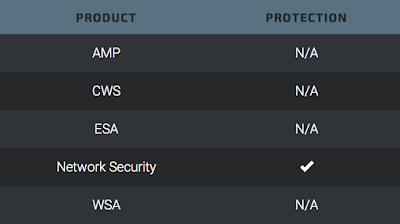
Talos has released rules that detect attempts to exploit these vulnerabilities to protect our customers. Please note that additional rules may be released at a future date and current rules are subject to change pending additional vulnerability information. For the most current rule information, please refer to your Defense Center, FireSIGHT Management Center or Snort.org.
Snort rules: 36536, 37841-37843.
Timeline
2016-02-11 - Vendor Disclosure
2016-04-26 - Vulnerability Patched
2016-04-26 - Public Release