Recently a large scale ransomware campaign delivering Samsam changed the threat landscape for ransomware delivery. Targeting vulnerabilities in servers to spread ransomware is a new dimension to an already prolific threat. Due to information provided from our Cisco IR Services Team, stemming from a recent customer engagement, we began looking deeper into the JBoss vectors that were used as the initial point of compromise. Initially, we started scanning the internet for vulnerable machines. This led us to approximately 3.2 million at-risk machines.
As part of this investigation, we scanned for machines that were already compromised and potentially waiting for a ransomware payload. We found just over 2,100 backdoors installed across nearly 1600 ip addresses. Over the last few days, Talos has been in the process of notifying affected parties including: schools, governments, aviation companies, and more.
Several of these systems had Follett "Destiny" software installed. Destiny is a Library Management System that is designed to track school library assets and is primarily used in K-12 schools across the globe. We contacted Follett, who described an impressive patching system that not only patches all systems from version 9.0-13.5, but also captured any non-Destiny files that were present on the system to help remove any existing backdoors on the system. Follett technical support will then reach out to customers who are found to have suspicious files on their system. It is imperative, given the wide reach of this threat, that all Destiny users ensure that they've taken advantage of this patch.
Follett asked us to share the following:
Based on our internal systems security monitoring and protocol, Follett identified the issue and immediately took actions to address and close the vulnerability on behalf of our customers.
Follett takes data security very seriously and as a result, we are continuously monitoring our systems and software for threats, and enhancing our technology environment with the goal of minimizing risks for the institutions we serve.
As part of this investigation, Talos and Follett will continue to work together to analyze the webshells found on compromised servers and to ensure that our customers are informed about how best to protect their networks.
In this process we've learned that there is normally more than one webshell on compromised JBoss servers and that it is important to review the contents of the jobs status page. We've seen several different backdoors including "mela", "shellinvoker", "jbossinvoker", "zecmd", "cmd", "genesis", "sh3ll" and possibly "Inovkermngrt" and "jbot". This implies that that many of these systems have been compromised several times by different actors.
US-CERT has published the following advisory regarding webshells:
https://www.us-cert.gov/ncas/alerts/TA15-314A
Webshells are a major security concern as it indicates an attacker has already compromised this server and can remotely control it. As a result, a compromised web server could be used to pivot and move laterally within an internal network.
Given the severity of this problem, a compromised host should be taken down immediately as this host could be abused in a number of ways. These servers are hosting JBoss which has been recently involved in a high profile ransomware campaign.
The software for the shell itself can be found here.
Recommended Remediation
If you find that a webshell has been installed on a server there are several steps that need to be taken. Our first recommendation, if at all possible, is to remove external access to the server. This will prevent the adversaries from accessing the server remotely. Ideally, you would also re-image the system and install updated versions of the software. This is the best way to ensure that the adversaries won't be able to access the server. If for some reason you are unable to rebuild completely, the next best option would be to restore from a backup prior to the compromise and then upgrade the server to a non-vulnerable version before returning it to production.
For users of Follett Destiny, please respect the autoupdate notifications and ensure that you have patched correctly. This process, according to Follett, should remove unwanted backdoor shells.
As always, running a reputable anti-virus software is recommended.
Conclusion
With around 2100 servers affected, there are a lot of stories about how this happened. But a consistent thread in them all is the need to patch. Patching is a key component to software maintenance. It is neglected by both users and makers of the software far too often. Failures anywhere along the chain will ensure that this type of attack remains successful. With the addition of ransomware, the potential impacts could be devastating for small and large businesses alike.
Indicators
This list is not meant to be comprehensive at this time, but provides for the basis to develop more Indicators that are present or left behind by various webshell and related actor tools.
| jbossass.jsp | jbossass_jsp.class |
| shellinvoker.jsp | shellinvoker_jsp.class |
| mela.jsp | mela_jsp.class |
| zecmd.jsp | zecmd_jsp.class |
| cmd.jsp | cmd_jsp.class |
| wstats.jsp | wstats_jsp.class |
| idssvc.jsp | idssvc_jsp.class |
| iesvc.jsp | iesvc_jsp.class |
Coverage
The following Snort rules address this threat. Please note that additional rules may be released at a future date and current rules are subject to change pending additional vulnerability information. For the most current rule information, please refer to your FireSIGHT Management Center or Snort.org.
Snort Rules
- JBoss Server Vulnerabilities: 18794, 21516-21517, 24342-24343, 24642, 29909
- Web Shell: 1090,21117-21140,23829,23830,27729-27732,27966-27968,28323,37245
- Samas: 38279,38280, 38304,38360,38361
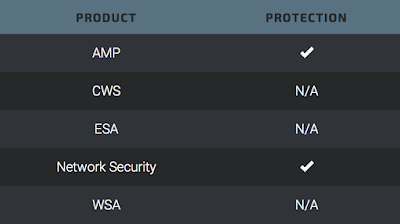
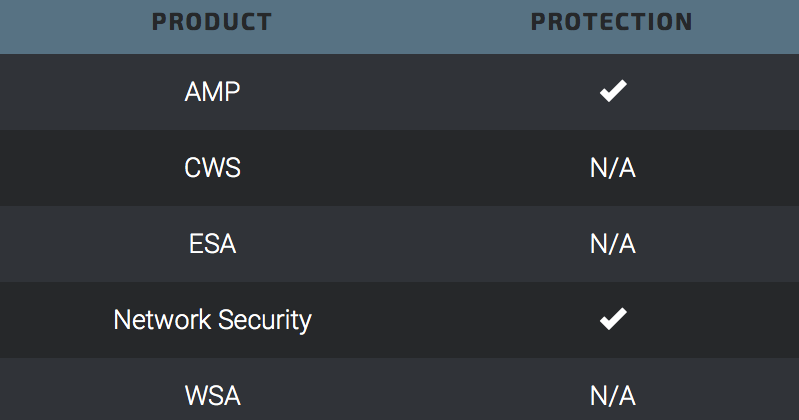
Additionally, Advanced Malware Protection (AMP) can help detect and prevent the execution of this malware on targeted systems.
Network Security encompasses IPS and NGFW. Both have up-to-date signatures to detect malicious network activity that this campaign exhibits.