Vulnerability discovered by Piotr Bania of Cisco Talos.
Cisco Talos, in conjunction with Apple’s security advisory issued on Mar 22, is disclosing the discovery of a local vulnerability in the communication functionality of the Apple Intel HD3000 Graphics kernel driver. This vulnerability was initially discovered by the Talos Vulnerability Research & Development Team and reported in accordance with responsible disclosure policies to Apple.
There is a local privilege escalation vulnerability in the Apple Intel HD3000 Graphics kernel driver (TALOS-2016-0088/CVE-2016-1743) which Talos has identified on OS X 10.11. Exploitation of this vulnerability requires user interaction, such as executing a malicious executable received via email or downloaded and run on the user's Mac. With OS X becoming more common in the workplace this can be especially impactful as the common user accounts often do not have root-level permissions.
Advisory Summary This vulnerability can be triggered by sending specially crafted IOConnectCallMethod request to the Apple Intel HD3000 Graphics driver, the faulting code is in the IOGen575Shared::new_texture function.
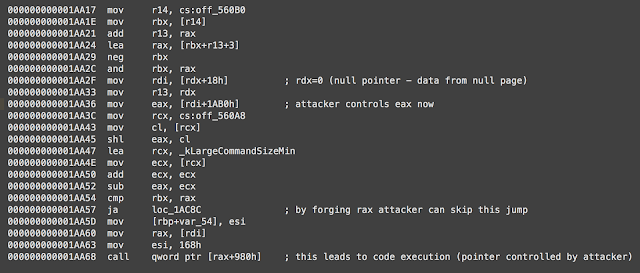
Successful exploitation can result in an escalated privilege for the attacker, who can then use root-level access for further malicious activity.
For full details please read the advisory here
Cisco Talos’ research and discovery of programmatic ways to find 0-days helps secure the platforms and software that our customers depend on. The disclosure of this and other vulnerabilities helps the entire online community by identifying security issues that otherwise could be exploited by threat actors. Uncovering new 0-days not only helps improve the overall security of the software that our customers use, but it also enables us to directly improve the procedures in our own security development lifecycle, which improves the security of all of the products that Cisco produces.
Related Snort rules: 37517, 37518
For the most up to date list, please refer to Defense Center or FireSIGHT Management Center.
For further zero day or vulnerability reports and information visit:
http://talosintel.com/vulnerability-reports/